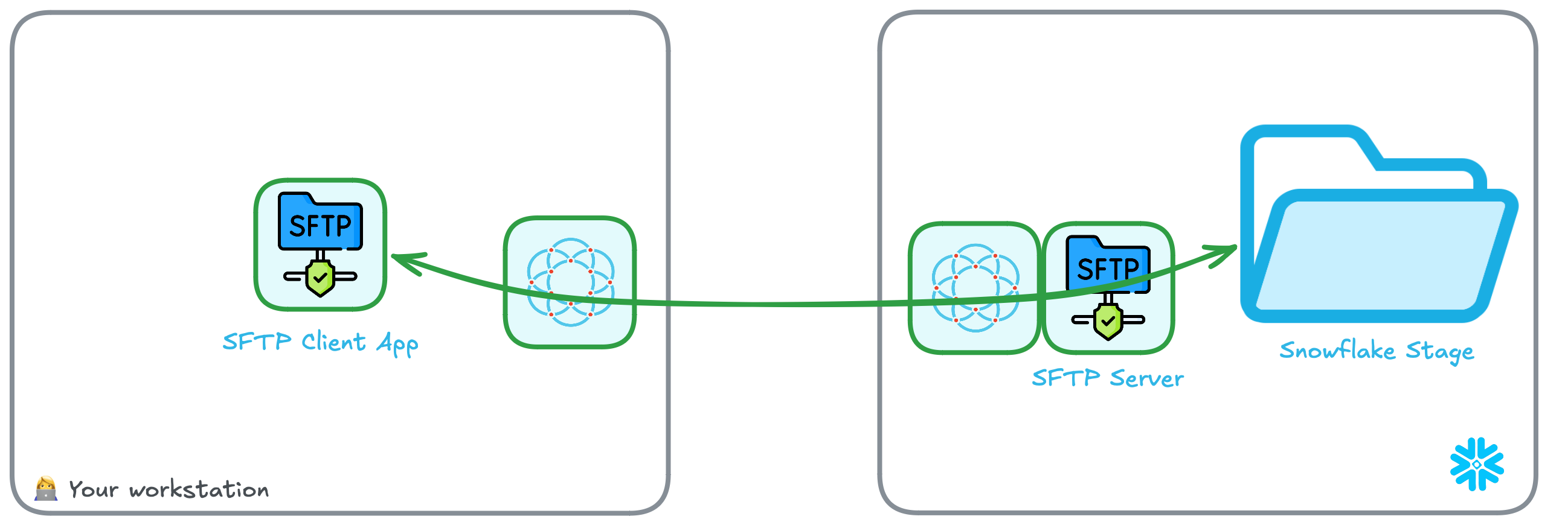
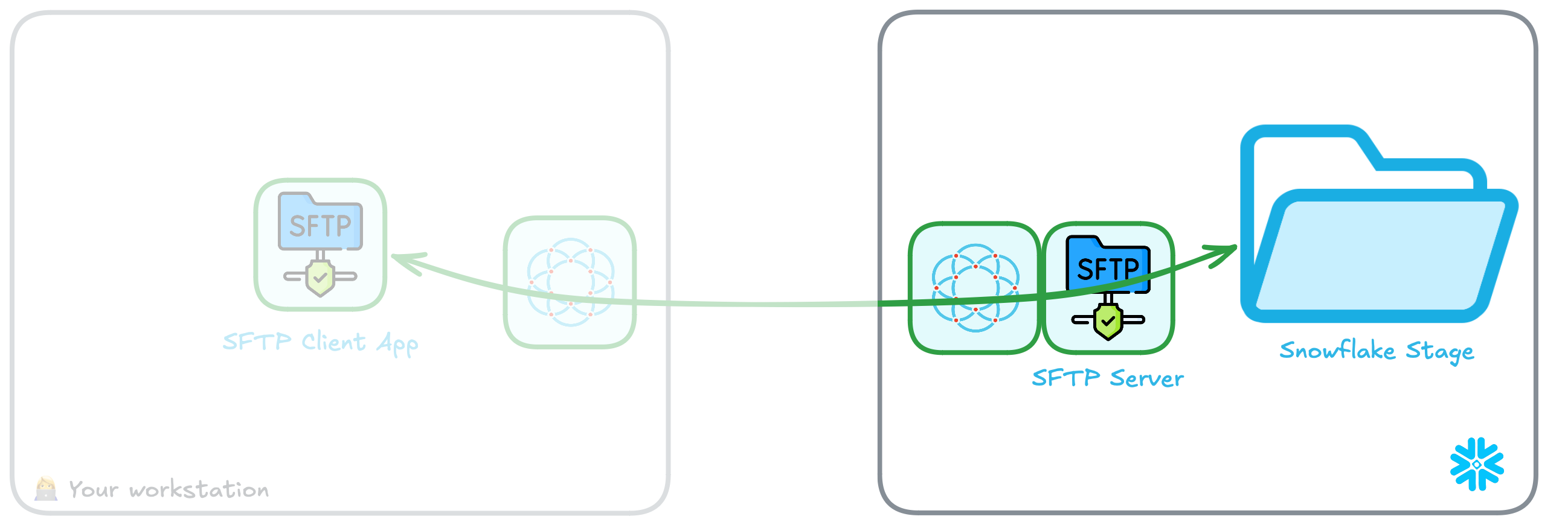
Access a Snowflake stage with SFTP
Glenn Gillen
VP of Product, GTM
With some systems the easiest way to move data around is by simply exporting files and uploading them to where you need them to be. One of the most ubiquitous ways to transfer files, especially among business critical systems that have been in place for many years, is via SFTP. Today I'm going to show you how you can setup your Snowflake Stage to serve as an SFTP server. Even better - it won't be necessary to manage IP allow lists, open firewall ports, or setup services like PrivateLink to make it happen.
The entire walk-through of setting this up and having everything working will take you less than 10 minutes.
Introducing the Snowflake Stage Data with SFTP Connector!
Quicklinks
Snowflake 💙 SFTP
SFTP, the Secure File Transfer Protocol, is an ubiquitous protocol for securely transferring files, based on the SSH (Secure Shell) protocol.
One way to import data into Snowflake is to use the snow command line client
or the snowflake-connector-python Python library to upload files and
have them be mapped to tables for later processing. Unfortunately, both those tools require a specific installation, and an OAuth authentication,
whereas SFTP is installed on many Linux distributions and only needs SSH keys.
In this post I'm going to show you how to securely access a Snowflake stage in your account, with SFTP, in just a few minutes. We will:
- Create a stage associated to your Snowflake account.
- Create an SFTP server on Snowflake with a private encrypted connection.
- Manage data on a Snowflake stage as though they were any other files in an SFTP client.
Create a stage
This can be done with just a few commands in the Snowsight editor:
_10-- create a test database_10CREATE DATABASE IF NOT EXISTS SFTP_TEST_DATABASE;_10USE DATABASE SFTP_TEST_DATABASE;_10_10-- create a test schema_10CREATE SCHEMA IF NOT EXISTS SFTP_TEST_SCHEMA;_10USE SCHEMA SFTP_TEST_SCHEMA;_10_10-- create an internal stage_10CREATE STAGE IF NOT EXISTS SECURE ENCRYPTION = (type = 'SNOWFLAKE_SSE');
The files contained in that stage can be listed with:
_10LIST @"SECURE";
And the stage should be empty for now!
Setup an SFTP server inside Snowflake
We are now going to create an SFTP server for the previous stage inside Snowflake. This will create a point-to-point connection between the two systems — without the need to expose any systems to the public internet!
Get the app
The Snowflake stage data with SFTP Connector by Ockam is available in the Snowflake Marketplace.
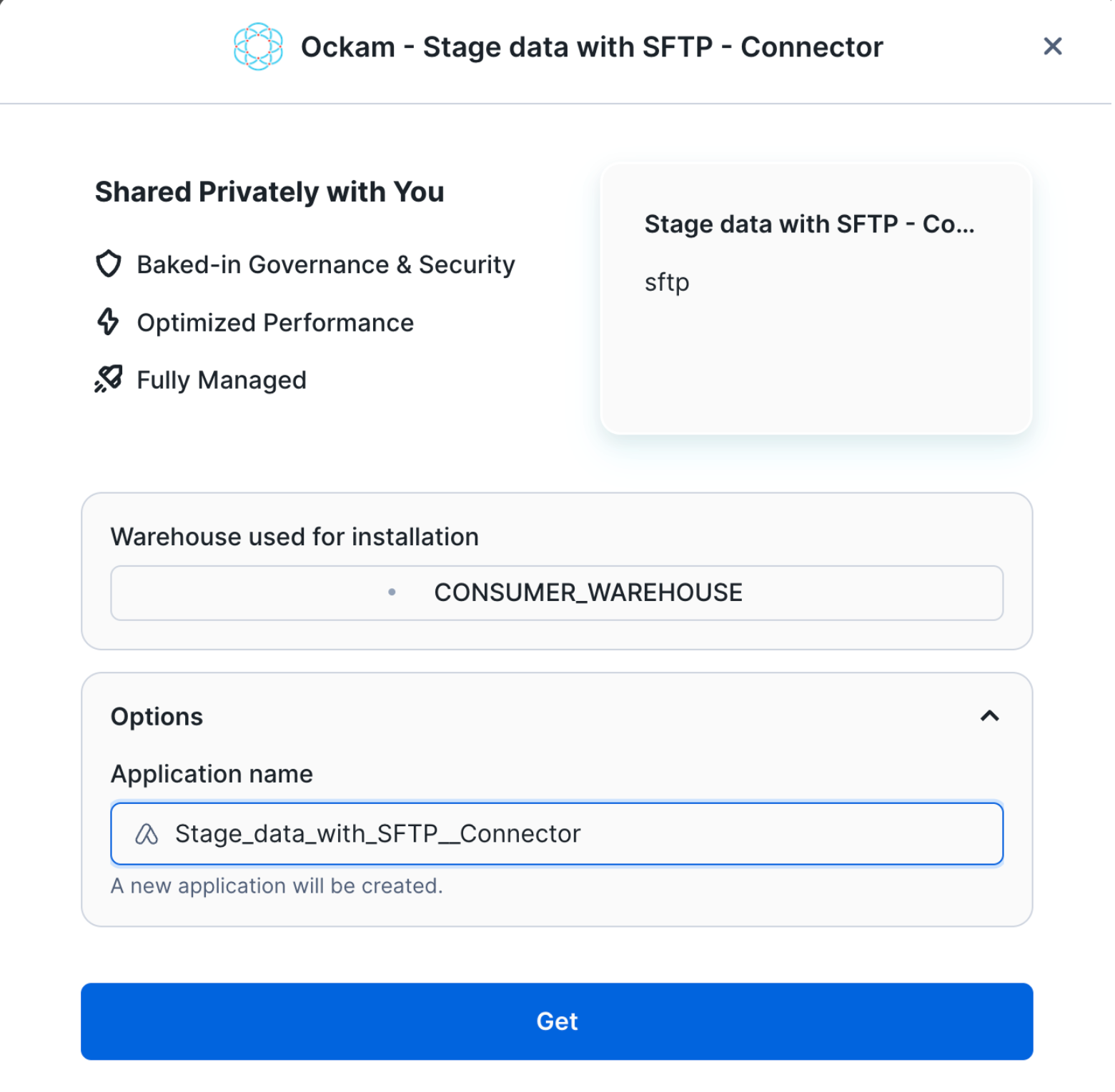
Select a warehouse
The first screen you're presented with will ask you to select the warehouse to utilize to activate the app and can choose to change the application name.
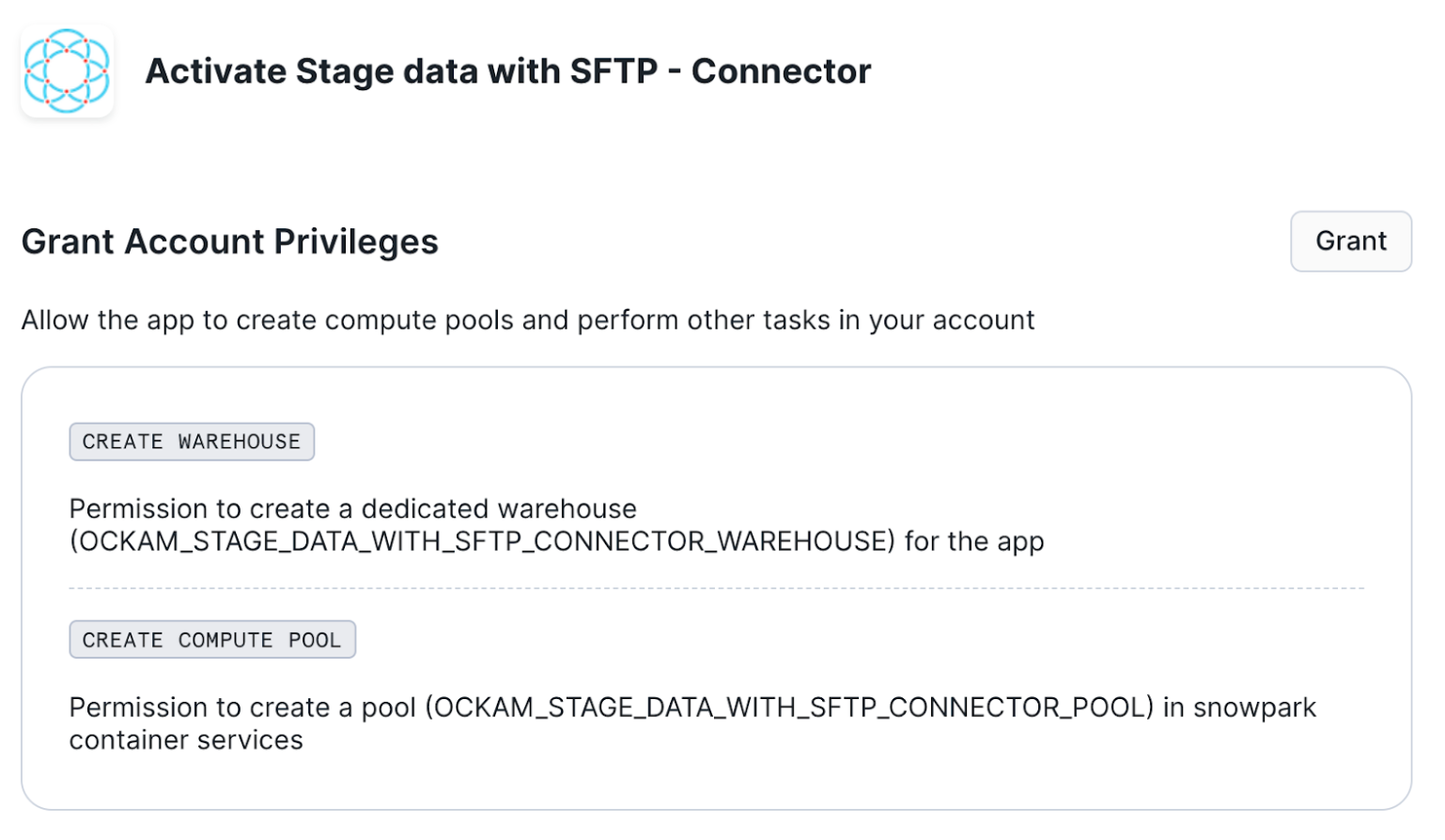
Grant account privileges
Click the Grant button to the right of this screen. The app will then be
automatically granted permissions to create a warehouse and create a compute
pool.
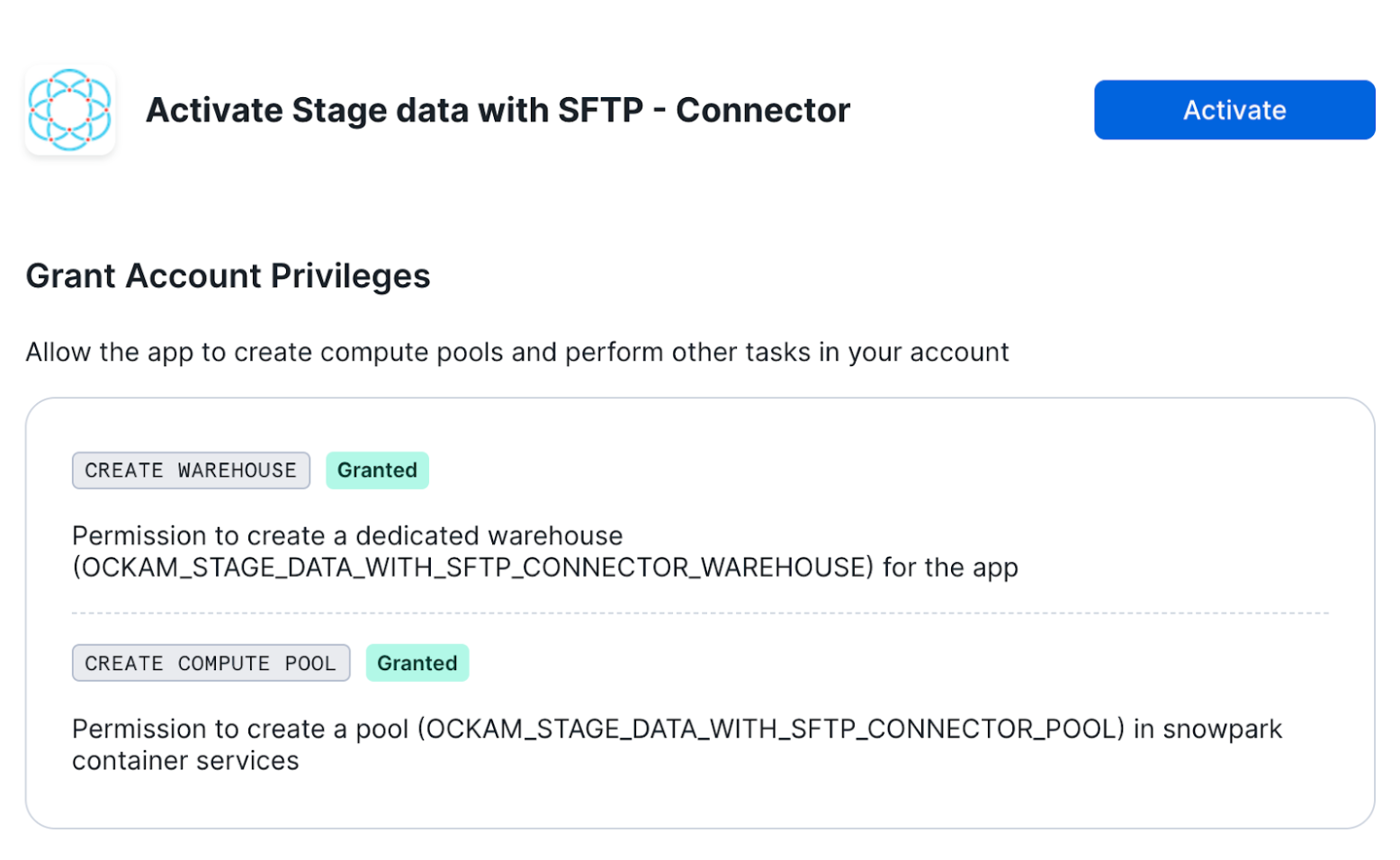
Activate app
Once the permissions grants complete, an Activate button will appear. Click
it and the activation process will begin.
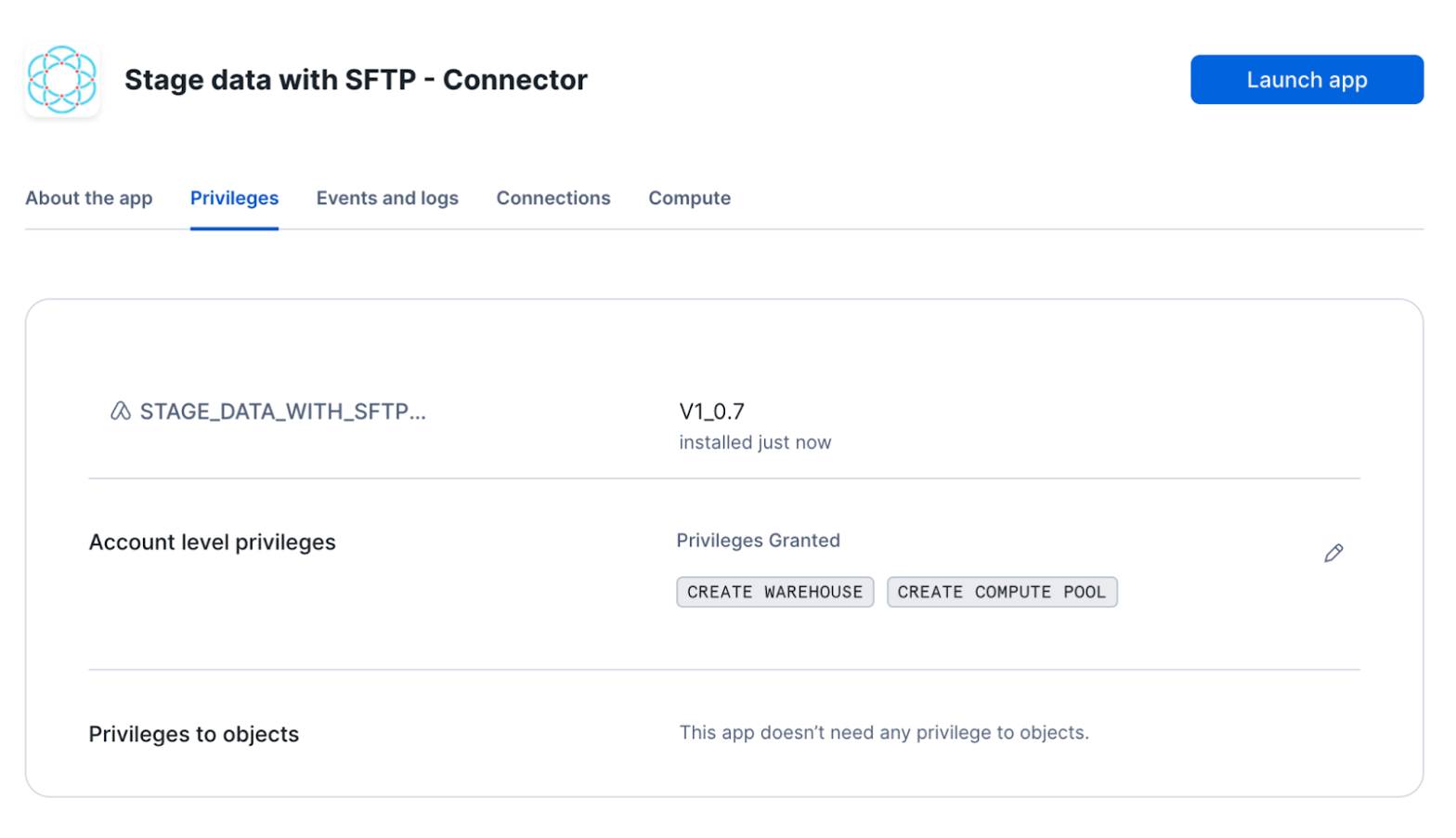
Launch app
After the app activates you'll see a page that summarizes the
privileges that the application now has. There's nothing we need
to review or update on these screens yet, so proceed by clicking the Launch app button.
Configuration
We are now going to configure the application. We first need to:
- Create an Ockam project and issue an enrollment ticket
- Create some SSH keys for both the SFTP server and the SFTP user.
Generating SSH keys
In order to setup both the SFTP server and the SFTP client, we will need to generate three SSH key pairs:
- One pair for the user.
- Two pairs for the server (we support both RSA and ED25519 signatures).
Configuring the application
Configure connection details
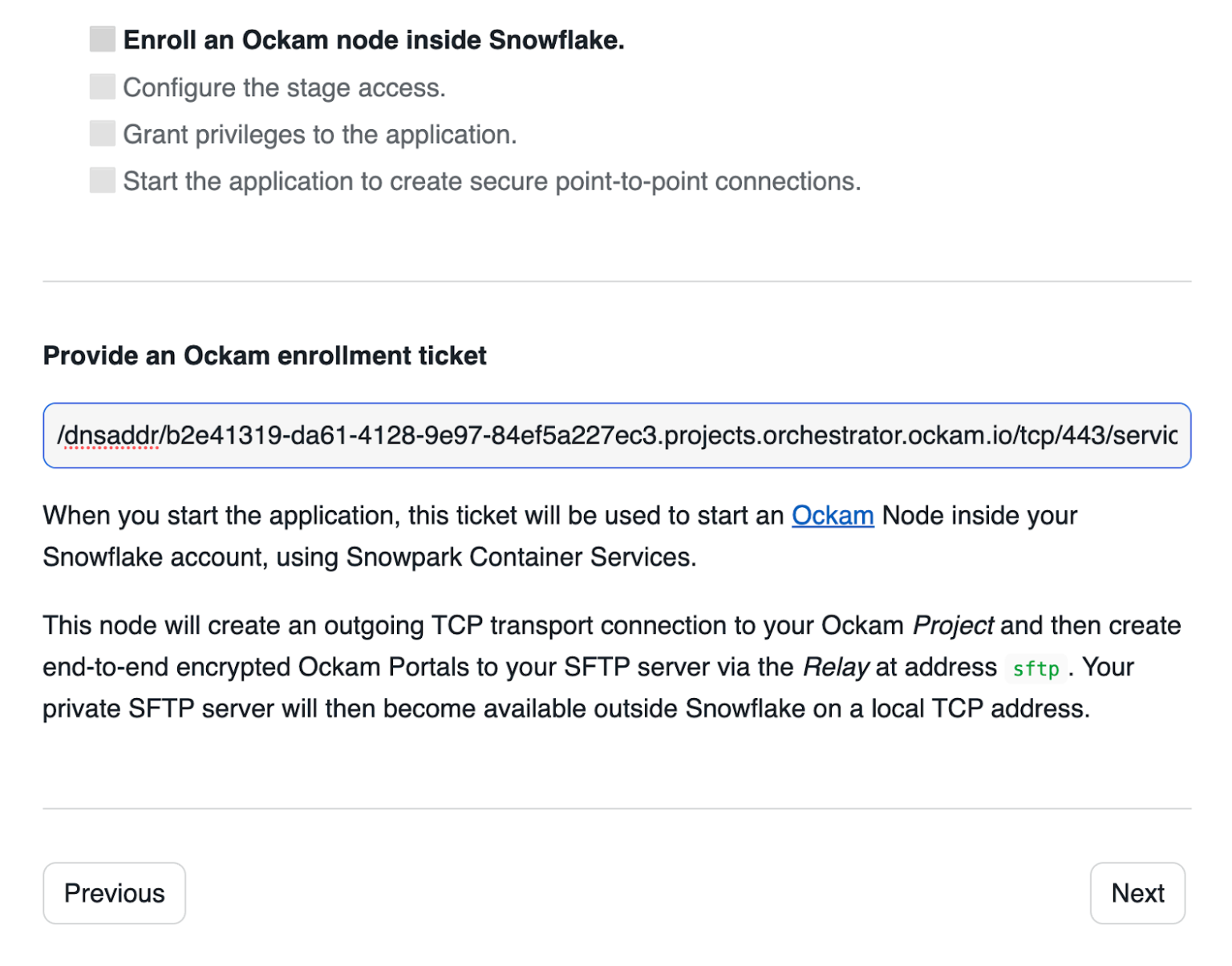
Click "Get started" to open the Snowflake setup screen.
Take the contents of the file sftp.ticket that we just created and paste
it into "Provide the above Enrollment Ticket" form field in the "Configure app"
setup screen in Snowflake.
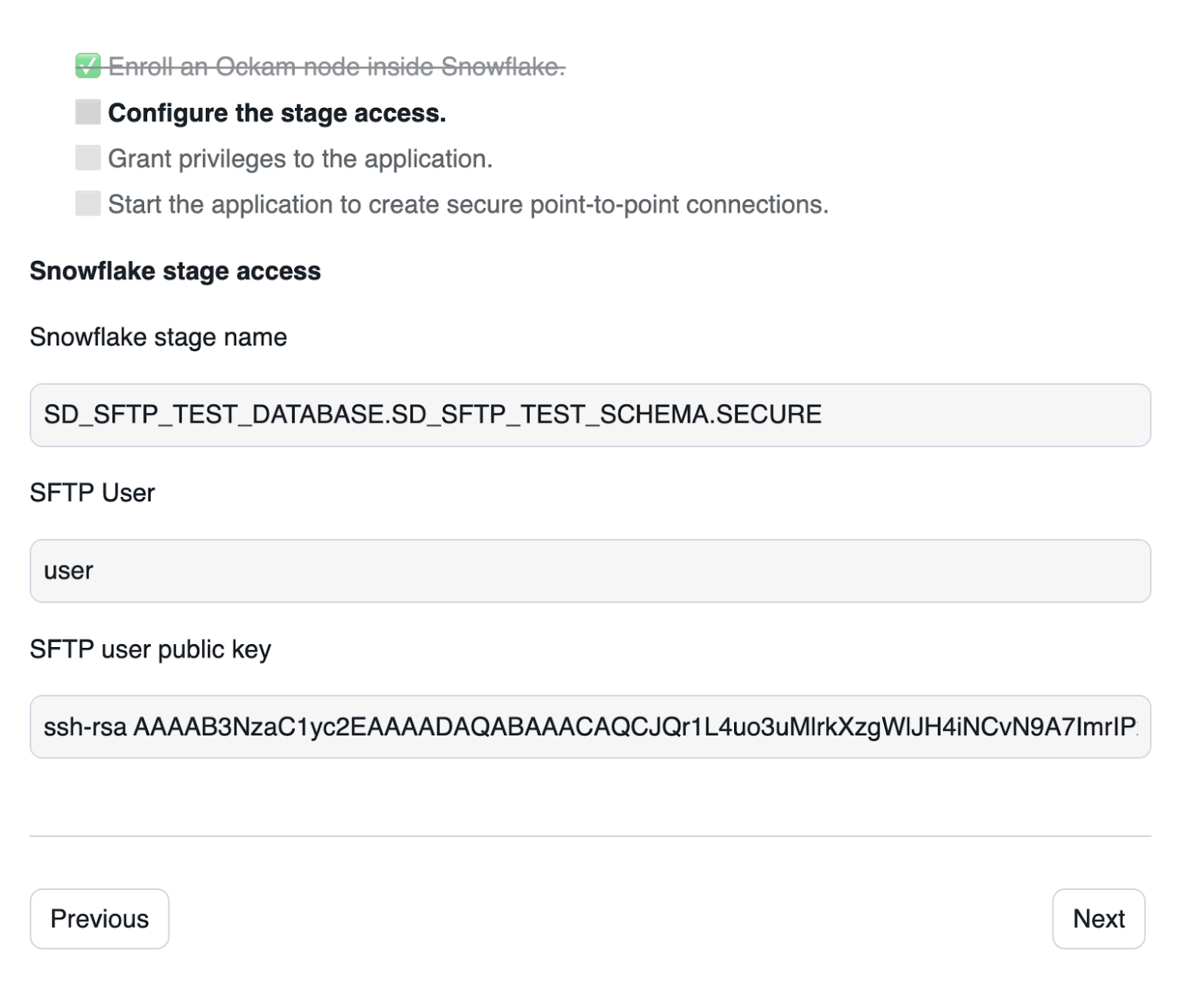
Configure the stage access
In this screen, we need to enter:
- The full name of the stage we want to access:
SFTP_TEST_DATABASE.SFTP_TEST_SCHEMA.SECURE. - The name of an SFTP user which will access the server, for example
user. - The public SSH key which we generated earlier: paste the content of the
id_rsa.pubfile.
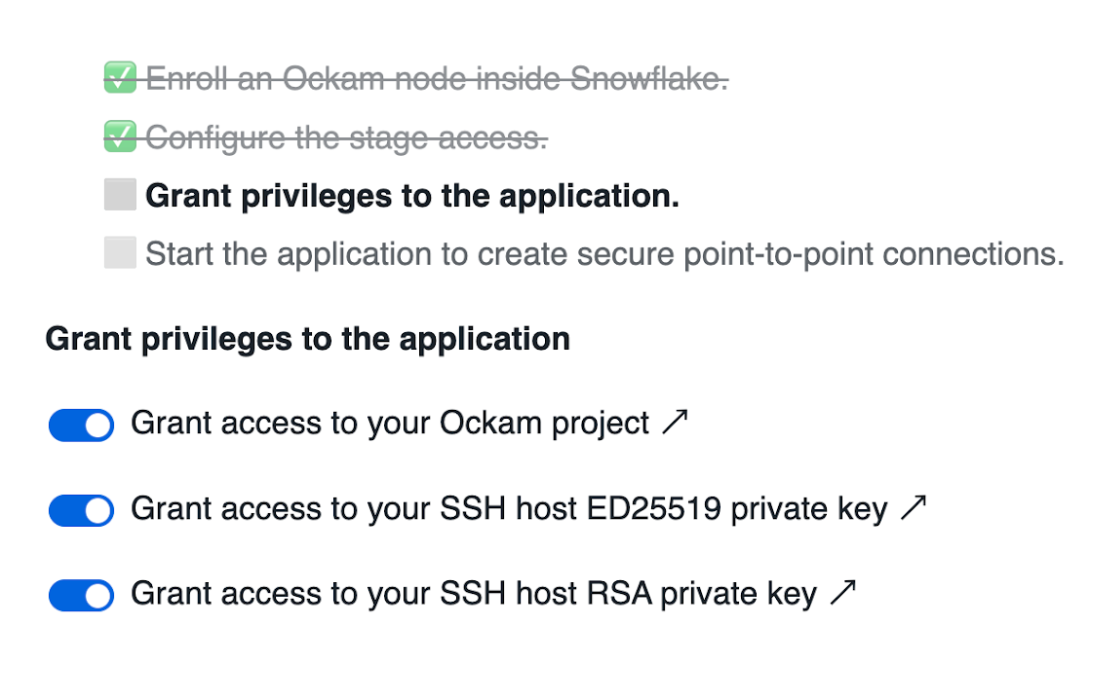
Grant privileges
To be able to authenticate with Ockam Orchestrator and then discover the route to our outlet, the Snowflake app needs to allow outbound connections to your Ockam project.
Toggle the Grant access to egress and reach your Project button and approve the connection by
pressing Connect.
Toggle the Grant access to your SSH host ED25519 private key button and paste the contents of the ssh_host_ed25519_key file.
Toggle the Grant access to your SSH host RSA private key button and paste the contents of the ssh_host_rsa_key file.
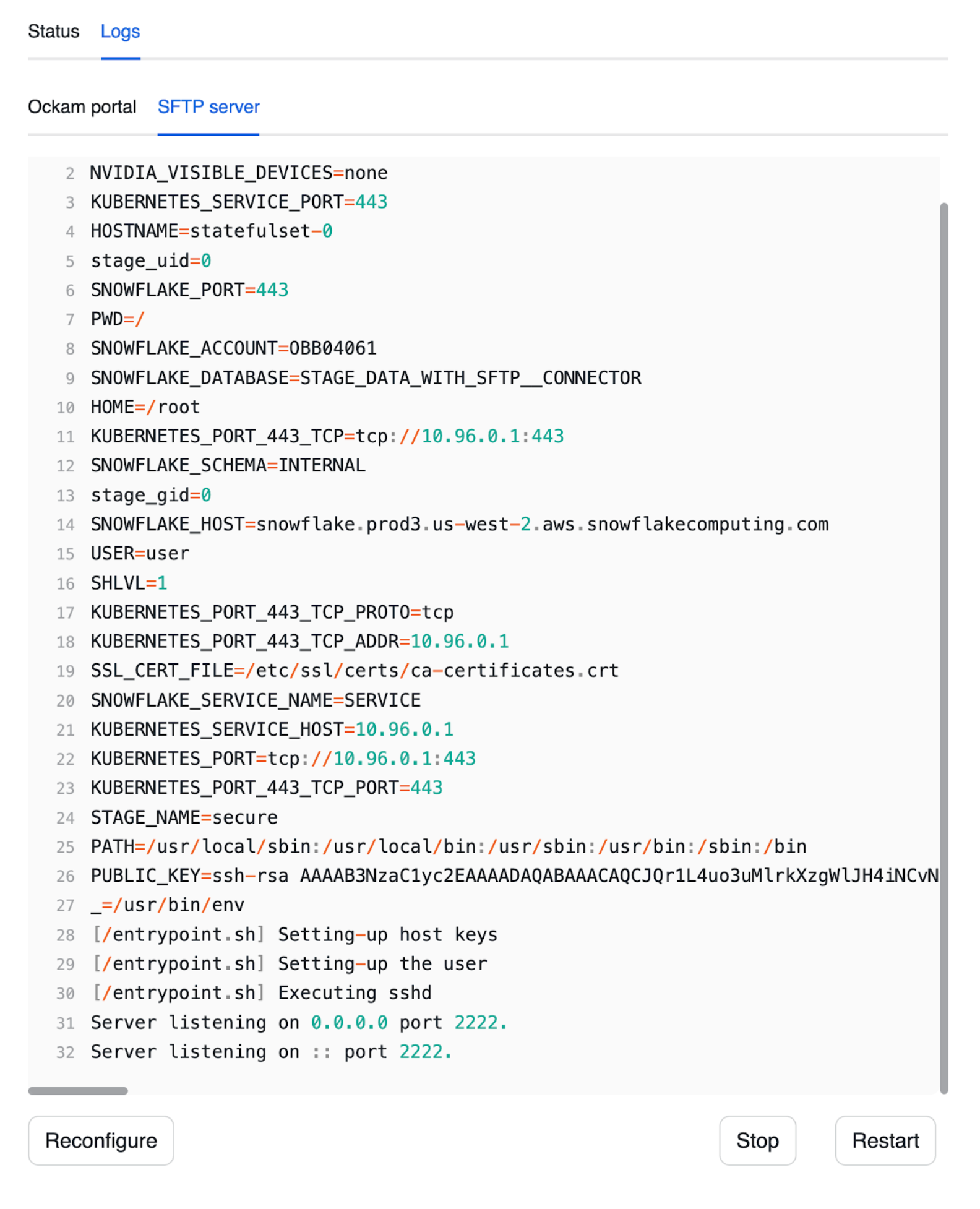
Start the SFTP server
Press "Next" and wait for the SFTP server to start. Once started, you should be able to check the SFTP server logs, and see that the server is listening on port 2222:
You can also notice a tab containing the logs for an Ockam node. That Ockam node is a portal outlet which:
- Created a relay named
sftpin the Ockam project. - Declares that only clients with the attribute
sftp-clientcan access the relay.
Connect the SFTP client
Testing the connection
Next steps
In summary, we are now able to securely access the contents of a Snowflake private stage, without exposing any port to the internet, with a few simple SFTP commands.
If you'd like to explore some other capabilities of Ockam I'd recommend:
- Creating private point-to-point connections with any database
- Adding security as a feature in your SaaS product
- Accessing a Snowflake Stage as a filesystem using WebDAV
Next Article
Secure & private connections to enterprise LLMs